Tools and tips round up: Email investigations, digging into payment gateways, and more
Plus: Google's new image search tool, tipsheets for search engines, shell companies, map investigations, and Telegram.

Over the last few weeks, a notorious fugitive drug kingpin and the head of Israel’s secretive military surveillance unit were exposed thanks to a similar OSINT technique.
Christopher Kinahan Sr is the reputed head of the the Kinahan cartel and among the world’s most wanted fugitives. He’s evaded capture for years. But Bellingcat connected him to a Google account that has left reams of reviews of restaurants and tourist attractions going back several years. Kinahan even posted photos that showed his partial reflection, aiding in the verification process.
Similarly, the identity of the head of Unit 8200, the Israeli military surveillance agency, was exposed this month by The Guardian, thanks in part to his use of a supposedly anonymous Gmail account and a related online trail.
In both cases, the reporters made use of techniques pioneered by a core OSINT tool, GHunt by mxrch. It enables you to pull information about a Google account, including the display name, avatar, and any public reviews posted by the account owner.
GHunt and the Holehe OSINT tool from megadose have helped inspire an explosion in tools for gathering data based on an email address. Now we have two powerful examples of how to use them in investigative work.
If you wan to learn more, Jake Creps of the excellent OSINT Newsletter recently published a free guide to different email search tools. And if you’re a paid subscriber, he did a step by step guide to installing and using GHunt.
Quick self plug: I recently published a story that revealed a U.S. federal task force is investigating the role of Chinese organized crime in a form of gift card fraud called “card draining.” We’ve been following the trail of gift card fraud since our Walmart investigation and it led us to Chinese money laundering organizations.
Read more here. You can also watch our explainer on how to avoid card draining. Please reach out if you have information to share about this or anything else worth looking into.
Tools and tips
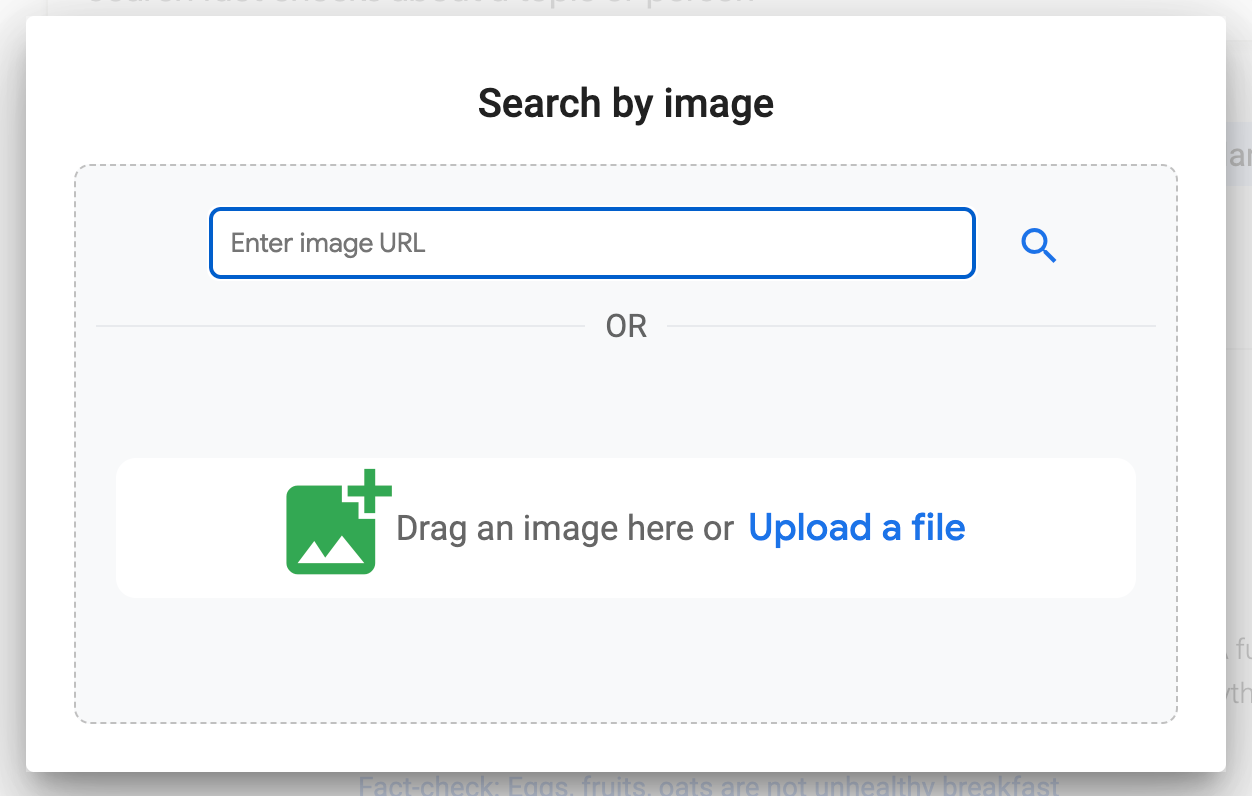
📍 Google released a publicly available version of its image context tool within Fact Check Explorer. I first shared details about this excellent app when it went into beta last summer. It’s a big upgrade on Google’s reverse image products!
📍 @GONZOs_int launched a new online version of their FactCheck Explorer Analysis Tool. It’s a nice way to filter and analyze data from Google Fact Check Explorer.
📍
created “Quick geolocation search.” It lets you enter latitude and longitude and search across a range of map, satellite, transport, and other services.📍 Her site also has “Quick archive.org viewer.” It allows you to “view multiple saved versions of a particular web page at the same time. One randomly selected for each year.”
📍 Dangerzone is a tool to that can scan for and remove malware from a variety of document types (PDFs, Microsoft Office, LibreOffice, images etc.). “Even if the original document is dangerous and would normally hack your computer, Dangerzone will convert it into a safe PDF that you can open and read,” wrote creator Micah Lee. (via GIJN)
📍 Chiasmodon is a multifaceted Python OSINT tool that can be used to gather details about a domain, Google Play app, email, and more. (via
)📍 The indispensable InVID WeVerify plugin launched a new AI generated voice detector tool and a multi-lingual fact check search.
📍 Epic Game Account Lookup lets you “search for an Epic account with an account ID, Epic, PSN, or Xbox Gamertag.” (via @0xtechrock)
📍 Lolarchiver launched the Database Search Engine, which lets you perform domain, name and keyword searches across more than 1,300 databases.
📍 MW Metadata lets you grab “details about a YouTube video and its uploader, playlist and its creator, or channel.” (via My OSINT News)
Webinars worth attending
🖥️ The Pulitzer Center announced The AI Spotlight Series, an exciting new program “to equip reporters and editors—whether on the tech beat or any other—with the knowledge and skills to cover and shape coverage of AI and its profound influence on society.” It includes a webinar series and resources. More info here.
🖥️ Jonathan Soma, the Knight Chair in Data Journalism at Columbia's Journalism School, is giving a series of free workshops called “Practical AI for (investigative) journalism.” Register here. The first session can be viewed here, and here’s a Google Doc with related links.
🖥️ Investigative Reporters & Editors is hosting “Investigating research fraud and errors: Tips and tools to help you get started.” Note: it’s only open to IRE members.
🖥️ GIJN is hosting “Investigating the Israel-Hamas Conflict.”
Worth watching
Here’ a recording of the excellent recent GIJN panel, “Investigating Elections: Threat from AI Audio Deepfakes”
Worth reading
📚 Kolina Koltai wrote “How to Get Started: Investigating Payment Gateways Online.” Read that along with a post from Griffin Glynn that explains how to grab a profile photo from someone’s Cash App QR code.
📚 Alex Lozano published a helpful OSINT Cheat Sheet for using search engines.
📚 Rowan Philp of GIJN looked at “Tips for Linking Shell Companies to their Secret Owners.”
📚 GIJN also wrote up the tools and techniques shared by Jane Lytvynenko in her recent Telegram OSINT workshop.
📚 Reza Rashidi wrote, “OSINT Method for Map Investigations” Lots of great tools and examples in this post.
📚 XoX wrote, “Google Hacking: Google Dorks for Sensitive Information”
📚 Nihad D. Hassan wrote, “Collecting OSINT on Discord: a guide” (via
)📚 Christo Buschek and Jer Thorp wrote “Models All The Way Down.” It’s a great visual investigation of LAION-5B, a key open source dataset that’s used to train popular AI models such as Stable Diffusion.
📚 The OSINT Guide wrote, “Investigate Companies in Europe: general resources.”
📚 Miriam Forero Aziza wrote, “Tipsheet for Using Ocean Data in Your Investigations”
📚 Dr. Augustine Fou wrote, “Detect AFFILIATE fraud with FouAnalytics, save millions”
📚 A new study published in Nature looks at “Persistent interaction patterns across social media platforms and over time.” The authors write, “Drawing from an extensive dataset that spans eight platforms over 34 years—from Usenet to contemporary social media—our findings show consistent conversation patterns and user behaviour, irrespective of the platform, topic or time.”
That’s it for this edition of Digital Investigations! Thanks for reading. You can find me on Threads, Bluesky, Mastodon, and LinkedIn. I’m not very active on Twitter these days.